Zip Password Recovery Magic: Unlocking Your Files
Losing access to important files due to a forgotten password can be incredibly frustrating, especially when those files are compressed within a zip archive secured with a seemingly impenetrable password. Thankfully, "zip password recovery magic" isn't just a catchy phrase, it's a reality thanks to various techniques and tools available. Let's delve into the world of zip password recovery and explore the magic that can unlock your precious data.
Understanding Zip Passwords and Encryption
Before diving into recovery methods, it's crucial to understand how zip passwords and encryption work. When you protect a zip file with a password, the archive employs encryption algorithms to scramble the data, making it unreadable without the correct key – your password.
The strength of this encryption varies depending on the zip software used and the chosen encryption method. Older zip versions might use weaker algorithms like "ZipCrypto," while newer ones often utilize more robust methods like "AES encryption." This difference in encryption strength significantly impacts the complexity and time required for password recovery.
Zip Password Recovery Methods: Unleashing the Magic
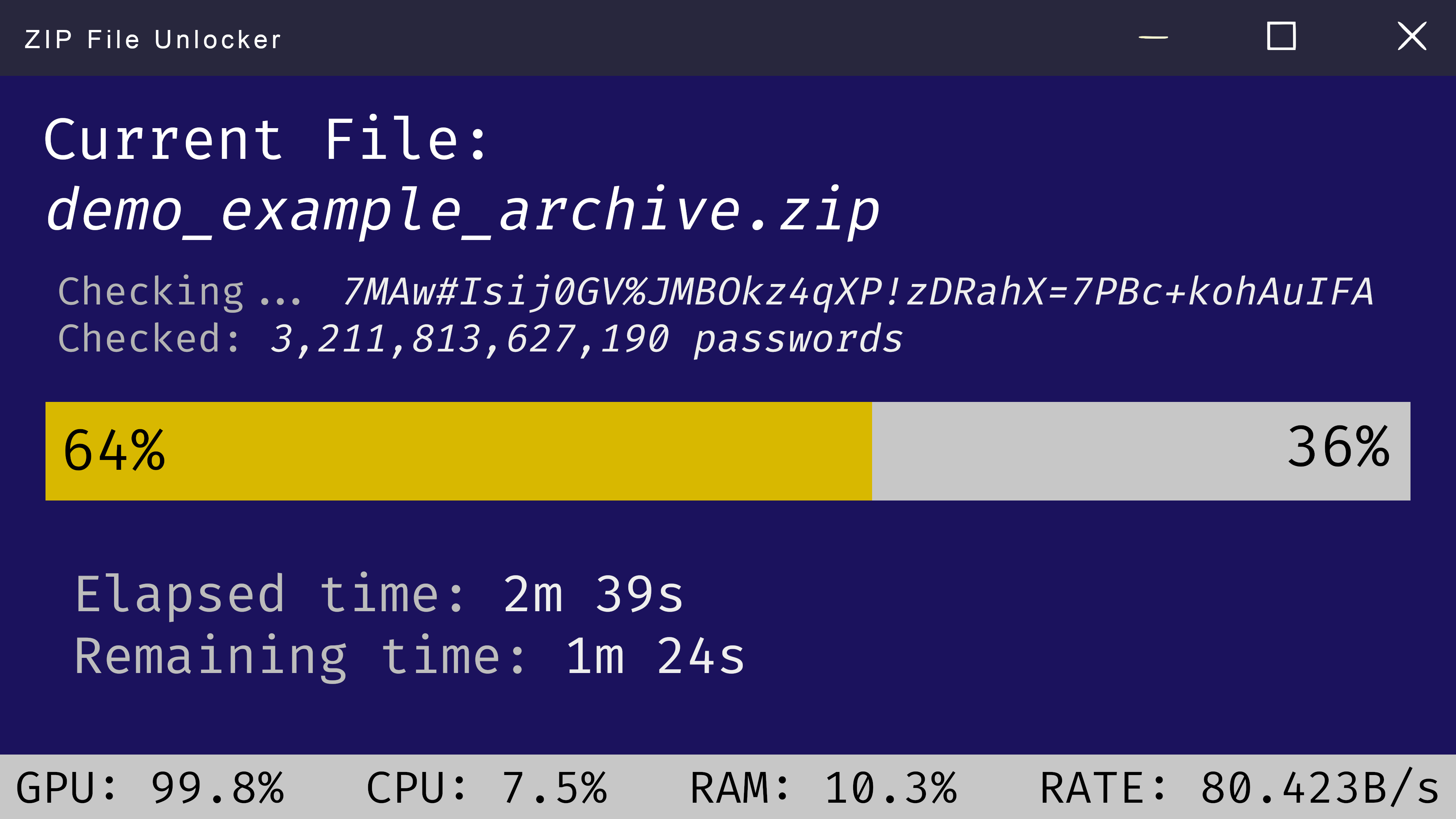
1. Brute-Force Attacks: A Trial-and-Error Approach
Brute-forcing involves systematically trying every possible password combination until the correct one is found. This method can be effective for short and simple passwords but becomes increasingly time-consuming and computationally expensive for longer, more complex ones.
Several tools are available online and offline that specialize in brute-force attacks for zip passwords. These tools often allow customization, letting users define a character set (numbers, symbols, uppercase/lowercase letters) to narrow down the possibilities.
2. Dictionary Attacks: Harnessing the Power of Words
Unlike brute-force, which randomly tries combinations, dictionary attacks utilize lists of common words, phrases, and passwords. This method proves particularly effective if the forgotten password resembles a commonly used word or phrase.
Various online resources offer comprehensive dictionaries for password cracking. Additionally, users can often customize these dictionaries by adding personalized words or variations relevant to the zip file's content or the user's habits.
3. Mask Attacks: Exploiting Known Password Patterns
If you recall specific details about your forgotten password, such as its length, the combination of uppercase and lowercase letters, or the presence of special characters, a "mask attack" can be incredibly useful. This method allows you to define a password template or "mask," significantly reducing the number of combinations to be tested.
For instance, if you remember your password was eight characters long, started with a capital letter, and included two numbers, you could set a mask like "A??????12". This significantly narrows down the search space, making the recovery process much faster.
4. Utilizing Password Recovery Software: Specialized Tools for the Job
Numerous dedicated software applications are specifically designed for zip password recovery. These tools often combine multiple attack methods, including brute-force, dictionary attacks, and mask attacks, providing a comprehensive solution.
Some popular options include:
- Advanced Archive Password Recovery: Known for its speed and support for various encryption algorithms.
- Passware Zip Password Recovery: Offers a user-friendly interface and a range of attack customization options.
- Accent ZIP Password Recovery: Boasts a high success rate and supports GPU acceleration for faster cracking.
Choosing the Right Recovery Method: Factors to Consider
The optimal zip password recovery method depends on several factors:
- Password Complexity: Short, simple passwords are susceptible to brute-force or dictionary attacks, while longer, more complex ones might require specialized software and significant time.
- Available Resources: Powerful computers with dedicated GPUs can significantly speed up brute-force attacks.
- Time Sensitivity: If time is of the essence, employing a combination of attack methods or opting for professional recovery services might be necessary.
Preventing Future Lockouts: Tips for Secure Password Management
While zip password recovery methods can be lifesavers, prevention is always better than cure. Here are some tips for secure password management:
- Use Strong and Unique Passwords: Employ a combination of uppercase and lowercase letters, numbers, and symbols. Avoid common words or easily guessable patterns.
- Leverage a Password Manager: These tools securely store and manage your passwords, eliminating the need to remember them all.
- Enable Two-Factor Authentication: Add an extra layer of security to your accounts by requiring a second verification factor, such as a code sent to your phone.
Zip password recovery magic is a powerful tool in desperate situations. However, understanding the importance of strong passwords and secure password management practices is crucial for preventing future lockouts and safeguarding your valuable data.
Unlock the power of prevention and keep your digital life secure.

 Windows
Windows MacOS
MacOS Linux
Linux