How to Access a File with a Password?
In today's digital age, protecting sensitive information is paramount. Password-protecting files offers a robust layer of security, restricting unauthorized access. But what if you need to access a password-protected file and can't recall the password? This article outlines various methods on how to access a file with a password, ranging from built-in operating system features to specialized software solutions.
Understanding File Password Protection
Before diving into the methods, it's essential to grasp the different ways files are password-protected:
- File-Level Encryption: This method uses algorithms to encrypt the entire file, making it inaccessible without the correct password.
- Password to Open: This common method sets a password required to open and view the file's contents.
- Password to Modify: This restricts modifications to the file, allowing access for viewing but not editing.
Methods to Access Password-Protected Files
The approach to accessing a password-protected file depends on the type of protection and the software used to encrypt it. Here are some common methods:
1. Remember or Recover the Password
The most straightforward way is to try remembering or recovering the password:
- Check Common Locations: Look for password hints in notes, saved passwords in browsers, or password managers.
- Try Common Passwords: If you tend to use similar passwords, try variations of them.
- Contact the File Creator: If possible, reach out to the person who created the file and inquire about the password.
2. Utilizing Built-in Operating System Features
Both Windows and macOS offer built-in features that might help access password-protected files:
- Password Reset Disk: If you had created a password reset disk beforehand, you could use it to regain access to your files.
- Previous Passwords: In some cases, operating systems store previous passwords, which might grant you access.
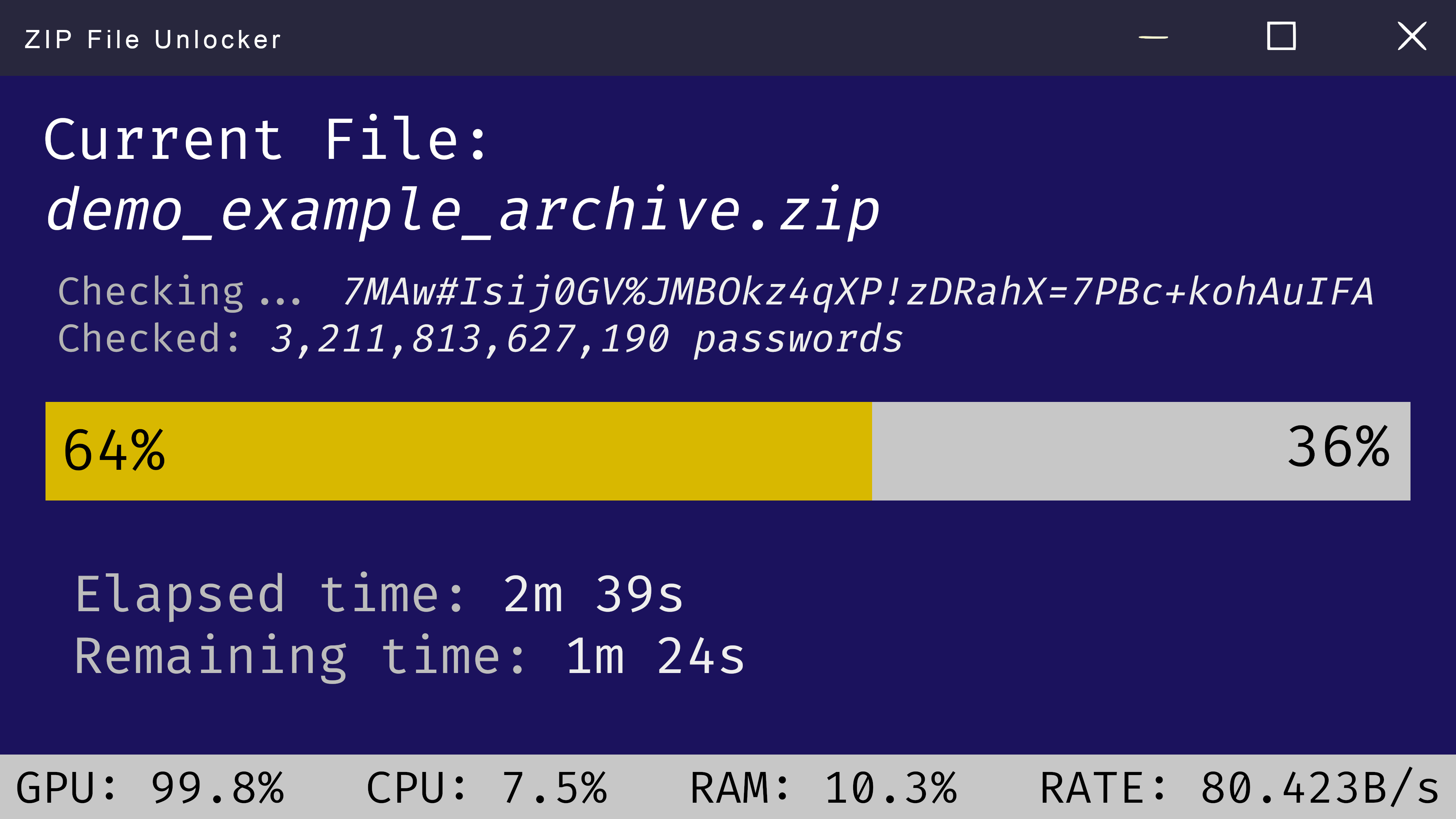
3. Employing Password Recovery Software
Numerous third-party password recovery tools are available that specialize in retrieving lost or forgotten passwords:
- John the Ripper: A popular free and open-source password cracking tool.
- Passware Kit: A comprehensive commercial software suite for password recovery from various file types and systems.
These tools utilize different techniques like brute-force attacks, dictionary attacks, and exploiting software vulnerabilities to crack passwords.
4. Seeking Professional Help
If all else fails, consider seeking help from data recovery specialists. These experts possess advanced tools and techniques to recover data from encrypted files.
Ethical Considerations
While these methods can help you access a password-protected file, it's crucial to use them ethically and legally. Attempting to access files that don't belong to you is unethical and potentially illegal.
Tips for Preventing Future Lockouts
- Use Strong, Unique Passwords: Employ a combination of upper and lowercase letters, numbers, and symbols.
- Leverage Password Managers: Store your passwords securely and conveniently with a password manager.
- Enable Two-Factor Authentication: Add an extra layer of security to your accounts.
Accessing a password-protected file can be challenging, but not impossible. By understanding the different methods and tools available, you can increase your chances of regaining access to your valuable data. Remember to prioritize ethical practices and take preventive measures to avoid future lockouts.

 Windows
Windows MacOS
MacOS Linux
Linux